Remote Infrastructure Automation Specialists in 24 Hrs!
Recruit the top offshore remote Infrastructure Automation Specialists, including expert software engineers, consultants, technical leads, and architects through RapidBrains. Our talent marketplace provides access to dedicated full-time developers on a contract basis. Build your team with affordable professionals skilled in Hydrogen, React Native, Storefront API, front-end and back-end technologies
List all Infrastructure Automation SpecialistsThe smartest way to hire remote developers on contract
Hire the best talent worldwide
Gain access to a talent pool of 500,000 and hire top developers from anywhere in the world.
Reduce employee cost by 70%
Hire remote developers with strong technical and communication skills at an affordable rate of 12 USD per hour
Expand without a legal entity
We ensure compliance with local labor laws and provide legal insulation when you hire dedicated developers
Zero hiring cost
Hire offshore developers, interview talents free of cost, and pay only when they start working
Daily work report
Stay updated on project progress with daily work reports from offshore experts.
Time monitoring tool
Track work hours accurately and ensure productivity with a powerful time monitoring tool.
Employee management portal
Manage your global team effortlessly with a user-friendly employee management portal.
Payroll management
Streamlined payroll management, so you can focus on growth without administrative worries.
Talent marketplace to hire the top
Developers.,Architects.,Technical Leads.,Consultants.
Experience the future of remote hiring!
Partner with us to access the best brains in the world
Our mission is to help companies boost profitability by optimizing workforce costs, while our vision is to create opportunities for all by seamlessly connecting the right talent with the right organizations.
500k+
Total talents
85+
Countries served
1.5k+
Happy customers
16+
Years in industry
Connect with Top Talent Around the World!
Trusted by 1.5K+ customers, we connect you with expert Shopify React contract developers.
The process flow
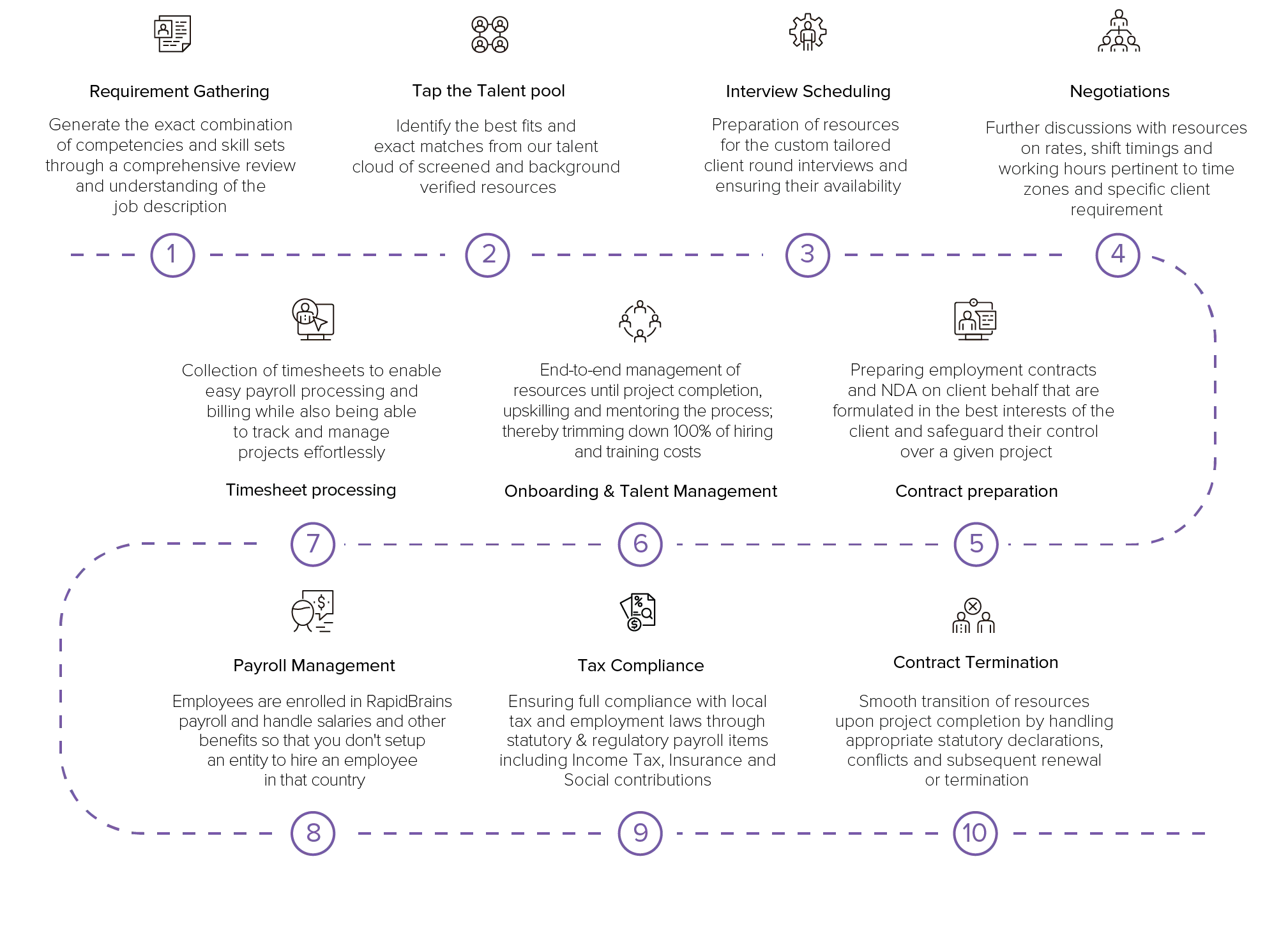
RapidBrains screening process

Structured screening & technical evaluation
With a pre-vetted talent pool of 500,000+ skilled remote developers, candidates undergo in-depth assessments with our in-house technical experts to validate their experience, technical proficiency, and problem-solving abilities.
- Comprehensive First-Level Evaluation Conducted by Our In-House Experts
- Evaluation of past project experience & problem-solving skills
- Communication & soft skills assessment for remote work readiness

On-Demand skill assessment based on client specification
We offer customized skill assessments based on client requests. Clients can select from a variety of evaluation methods to ensure the best talent fit.
- Technology-specific coding tests & project-based evaluations
- Live coding challenges & pair-programming sessions
- Integration with client-preferred interview or assessment platforms

Background verification & compliance assurance
We ensure a thorough verification process before onboarding, covering employment history, identity checks, and legal compliance.
- Advanced background & identity verification with employer references
- Final interview for cultural fit & client approval
- Onboarding & legal compliance handling, including payroll & contracts
Essential Skills for Infrastructure Automation Specialists
Infrastructure Automation Experts automate and operate IT infrastructure with code. They increase scalability, consistency, and efficiency through the use of tools such as Terraform, Ansible, and CI/CD pipelines for simplifying deployments, configurations, and system operations.
Infrastructure as Code (IaC)
Capacity to define and configure infrastructure with code for versioning and consistency.
Scripting and Automation
Familiar with Bash, Python, or PowerShell to automate routine infrastructure management processes.
Configuration Management
Proficient in solutions such as Ansible, Chef, or Puppet to automate configurations and server provisioning.
CI/CD Integration
Bakes infrastructure workflows into CI/CD pipelines to support continuous delivery and fast deployments.
Cloud Platform Skills
Excessive technical competency in AWS, Azure, or GCP in order to function with scalable, automated cloud settings.
Monitoring and Logging
Utilizes observability solutions like Prometheus, Grafana, or ELK for monitoring and debugging.
Security and Compliance Automation
Automates patching, security policies, and auditing in order to ensure infrastructure remains compliant and secure.

















